Exlade Cryptic DiskProfessional will provide a simple and affordable way toprotect disks and disk partitions by encrypting them. The encrypteddata cannot be accessed without entering the password, even if ahacker gets access to a PC or the hard drive is stolen.
Exlade Cryptic Disk Professional uses the AES 256-bit encryptionalgorithm, the same type of encryption that NASA, the FBI and theDepartment of Defense use to protect their data. Encrypting anddecrypting takes one click and does not require a PhD inmathematics or computer science.
Exlade Cryptic Disk Professional can be used either at home or inthe office. The program supports multiple users with differentdegrees of access privileges, as set by the system administrator.Each user will then have access to the encrypted data that he orshe has the access rights to, but not to the data of others.
Naturally, Exlade Cryptic Disk Professional has been designed towork with hard drives, but the program can be used with removablestorage media, such as USB Flash drives.
Once the data is encrypted, the files cannot be accessed by anyperson who does not know the password. After decryption, all filesbecome accessible and the hard drive works normally.
Here are some key features of “Exlade Cryptic DiskProfessional”:
– Creation of virtual encrypted disks from container files andmounting them as separate disks
– Encryption of whole disk partitions (internal and removable) aswell as other drives (memory cards, pen drives, USBdrives, and more) without losing information
– Transparent (on-the-fly) data encryption which takes place inreal time and does not affect computer performance
– Deniable Encryption so that encrypted volumes do not contain anysignatures which could be used to prove that they areencrypted disks or containers
– Plausible Deniability, which allows creating hidden encrypteddisks multiply nested inside of each other(steganography)
– Support for using key files together with a password or insteadof a password, offering users flexibility in how they deploythe disk encryption software
– Powerful protection from brute force password attacks (bothdictionary attacks and true brute force attacks) inaccordance with PKCS #5 v2
– Reliable protection from keyloggers (built-in virtual keyboardfor entering passwords)
– Ability to use the disk encryption software on a computer withoutinstalling it beforehand (portable mode)
– Configurable automatic actions when an encrypted disk is mountedor dismounted: play a WAV file, or launch a program or scriptin the following languages: CMD Shell, Windows Scripts andPowerShell
– Support for different cryptographic algorithms to encrypt data:AES/Rijndael, Serpent, Twofish, Blowfish, CAST6
– Use of XTS data encryption mode, developed specially for diskencryption (IEEE 1619 standard)
– Support for cascade encryption (use of multiple cryptographicalgorithms to encrypt data in sequence) to improve thecryptographic strength provided by the disk encryption software,increasing encryption key size from 256 to 2944 bits in XTSmode
– Support for using different algorithms for header key derivation:HMAC-SHA-512, HMAC-RIPEMD- 256, HMAC-Whirlpool
– Ability to mount an encrypted container/disk using any free driveletter or an empty folder on an NTFS disk
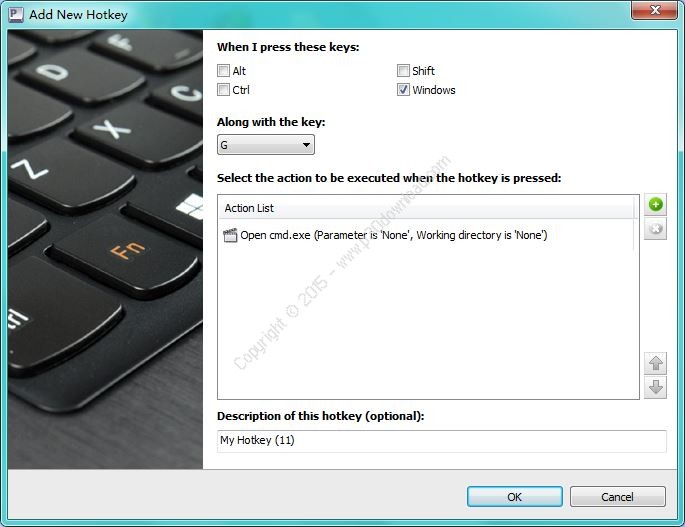
– Support for setting hotkeys to quickly mount and dismountencrypted volumes
– Support for automatic restoration of access settings to sharedresources on an encrypted disk after mounting it
– Optimization for multiple CPUs
– Ability to access the program’s features from the command line,which allows automating the process of working with theprogram
– Multilingual interface Creation of virtual encrypted disks fromcontainer files and mounting them as separate disks
– Encryption of whole disk partitions (internal and removable) aswell as other drives (memory cards, pen drives, USB drives,and more) without losing information
– Transparent (on-the-fly) data encryption which takes place inreal time and does not affect computer performance
– Deniable Encryption so that encrypted volumes do not contain anysignatures which could be used to prove that they areencrypted disks or containers
– Plausible Deniability, which allows creating hidden encrypteddisks multiply nested inside of each other(steganography)
– Support for using key files together with a password or insteadof a password, offering users flexibility in how they deploythe disk encryption software
– Powerful protection from brute force password attacks (bothdictionary attacks and true brute force attacks) inaccordance with PKCS #5 v2
– Reliable protection from keyloggers (built-in virtual keyboardfor entering passwords)
– Ability to use the disk encryption software on a computer withoutinstalling it beforehand (portable mode)
– Configurable automatic actions when an encrypted disk is mountedor dismounted: play a WAV file, or launch a program or scriptin the following languages: CMD Shell, Windows Scripts andPowerShell
– Support for different cryptographic algorithms to encrypt data:AES/Rijndael, Serpent, Twofish, Blowfish, CAST6
– Use of XTS data encryption mode, developed specially for diskencryption (IEEE 1619 standard)
– Support for cascade encryption (use of multiple cryptographicalgorithms to encrypt data in sequence) to improve thecryptographic strength provided by the disk encryption software,increasing encryption key size from 256 to 2944 bits in XTSmode
– Support for using different algorithms for header key derivation:HMAC-SHA-512, HMAC-RIPEMD- 256, HMAC-Whirlpool
– Ability to mount an encrypted container/disk using any free driveletter or an empty folder on an NTFS disk
– Support for setting hotkeys to quickly mount and dismountencrypted volumes
– Support for automatic restoration of access settings to sharedresources on an encrypted disk after mounting it
– Optimization for multiple CPUs
– Ability to access the program’s features from the command line,which allows automating the process of working with theprogram
– Multilingual interface
Installer Size: 13.11 MB
Download Links : Cryptic Disk Pro v3.0.29.569 + Crack