Software Description: Jetico BestCrypt v9.03.5 Keygen Serial
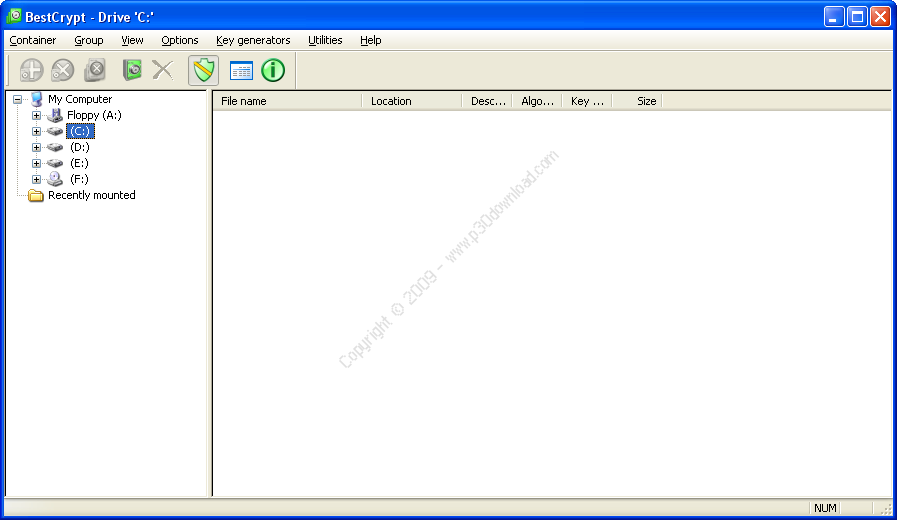
BestCrypt software will create and will supportencrypted virtual disks.
These disks are visible as regular disks with correspondent driveletters. The data stored on a BestCrypt disk is stored in thecontainer file.
A container is a file, so it is possible to backup a container,move or copy it to other disk (CD- ROM or network, for instance)and continue to access your encrypted data using BestCrypt.
Any free drive letter in the system may be used to mount and toopen an encrypted file-container for access. When the virtual diskis opened, you can read and write data as if it were a conventionalremovable disk.
How does BestCrypt work? BestCrypt creates a pre-encrypted filecalled
a container. This container is created by an encryption algorithm(Twofish,
Blowfish, Rijndael, or GOST28147-89).
In addition, BestCrypt creates a logical disk. The container islinked to a logical disk, and the disk is opened for access usingthe unique container password. All data stored in the logical diskare stored in the container in an encrypted form and transparentlyaccessible for an authorized person.
But there are few limitations here: Windows 95 and DOS operatingsystems do not support NTFS filesystem. So, if you format aBestCrypt container in Windows XP/2000/NT using the NTFSfilesystem, it will be impossible to mount the container on WindowsME/98/95/DOS computers.
Here are some key features of “BestCrypt”:
– 1. The BestCrypt software is designed for Windows95/98/ME/NT/2000/XP operating systems and satisfies allrequirements for 32-bit software. 32-bit BestCrypt Virtual DeviceDrivers are designed for Windows 95/98/ME and Windows NT/2000/XPfile systems and they use all available advantages of the operatingsystems.
– 2. There are no limitations to the number of local physicaldrives on which a user stores BestCrypt containers. Any type ofphysical media may be used to store and access the data on theBestCrypt containers: hard drives, removable media, magneto-opticaldevices, etc.
– 3. Any network accessible disk may be used by BestCrypt softwarefor creating and accessing file-containers. This network disk maybe shared by a server with any operating system, for exampleUNIX-like operating systems (OSF/1, LINUX, BSD, SunOS, HP/UX, AIXand others), Novell, Windows NT/2000/XP, Windows 95/98, Windows3.xx, etc.
– 4. User may copy (backup) BestCrypt containers from one computerto another in network and continue to access encrypted data withoutany limitation on the operating system type. For example, a usermay copy or move a file-container from a computer with a Windowsoperating system to a UNIX computer, yet continue access the data(now stored inside the container on the UNIX computer) from theWindows computer. Note that there is a separate version ofBestCrypt for the Linux operating system. For more details on thesoftware, you may visit our website:http://www.jetico.com/linux.htm .
– 5. Automatic closing options.
Timeout – if the timeout option is used: all virtual drivesautomatically close if the user has left computer or simply doesnot touch keyboard and mouse for the specified time (i.e. a “Screensaver” style time-out).
Hot Key – if Hot Key option is used: all virtual drives areautomatically closed if the user presses the Hot Key combination onthe keyboard.
– 6. Container Guard utility. This utility prevents the user fromdeleting an encrypted file-container, as well as preventing anunauthorized person who has network access to your computer fromdeleting your file-container. In Windows NT, 2000, and XP,Container Guard may be disabled only by an administrator.
– 7. BCWipe utility. To avoid an unauthorized restoring of deletedfiles from your disks, you can run BCWipe utility to wipe deletedfiles from the disk. The utility may also wipe all free space andfile slacks on the specified disk.
– 8. The main commands to control access to encrypted data may berun from Windows Explorer (“My Computer” window) without startingBestCrypt Control Panel. To run these commands from Explorer, youshould use the same method as for creating and opening any otherdocument from Explorer, for example, a Microsoft Word document.
– 9. BestCrypt has been designed with an extendible architecture:any third-party encryption software or hardware developers caninsert security extensions into the BestCrypt software – forexample, additional encryption algorithms, proprietary proceduresof entering the passwords, or additional hashing algorithms. To getadditional information about the architecture, visit the Jeticowebpage.
– 10. The BestCrypt Development Kit (available for downloading fromthe Jetico, Inc. Web site: http://www.jetico.com/bdk.htm) containsthe source code of all BestCrypt modules responsible for thesecurity of the software.
– 11. BestCrypt automatically saves information concerning whetherto share BestCrypt logical drives on a network. Now user does notneed to share the BestCrypt drives every time he/she rebootsoperating system.
Installer Size: 26.1 MB
Download Links : Jetico BestCrypt v9.03.5 + Crack