ScreenShots: Software Description: Ransomware has become a more serious problem in recent years; itspreads through e-mail attachments, infected programs andcompromised websites. Once infected by ransomware, your PC orimportant files can be encrypted by hackers that demand a ransom tolet you regain access. Nowadays, the outbreak of WannaCryRansomware already encrypted more than 200,000 computers worldwide.And the
Download LanAgent Standard v5.3.2.0 Keygen Crack
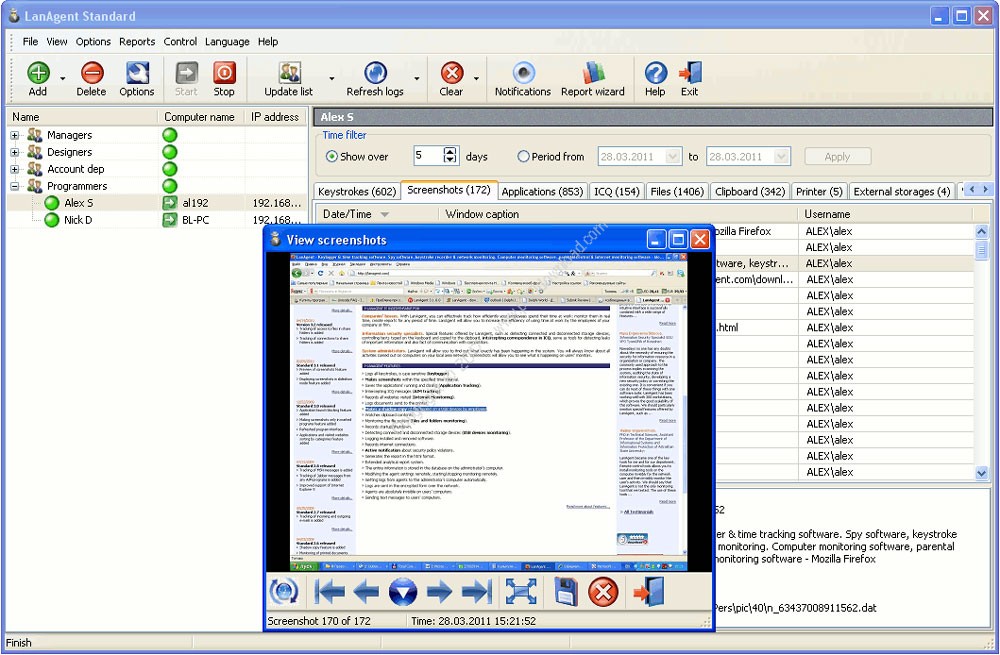
ScreenShots: Software Description: LanAgent is a computer monitoring software andcomputer tracking software. It controls and monitors activity onany computer connected to the local area network of yourorganization. The program allows you to detect the activities thathave nothing to do with work and will show you how efficiently youremployees spend their office hours. It is also
>Download Malwarebytes Anti-Rootkit v1.01.0.1020 Beta + Full Crack
Malwarebytes Anti-Rootkit is a handy andreliable application designed to scan, detect and clean maliciousrootkits that reside on your computer. The archive also includes a handy utility that repairs the damagecaused by the presence of rootkits. This operation requires areboot in order to apply the fixes. Setup+Crack Size: 12.7 MB Download Links > Malwarebytes Anti-Rootkit v1.01.0.1020
Windows Firewall Control v5.1.1.0 Full Crack
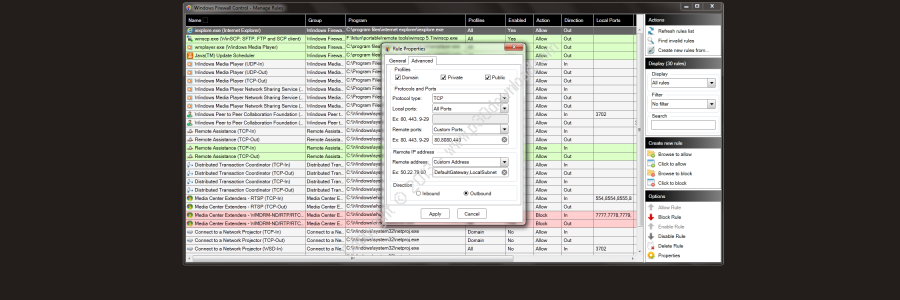
ScreenShots: Software Description: Windows Firewall Control is a handy andreliable utility designed to extend the functionality of theWindows Firewall and to provide quick access to its most frequentoptions. It runs in the system tray and allows user to control the nativefirewall easily without having to waste time by navigating to thespecific part of the firewall.
Avast! Offline Update 2017-09-23 Full Crack
ScreenShots: Software Description: Avast! Offline Update 2017-09-23 Full Crack Description Not Available Installer Size: 108 + 228 MB Download Links : Avast! Offline Update 2017-09-23 Keygen Serial
Download> Comodo Internet Security Premium 10.2.0.6526 Final X86/x64 – Comodo Internet Security Keygen Crack
ScreenShots: Software Description: Protects The SystemAgainst Malicious Code With Comodo InternetSecurity ComodoInternet Security Premium 10.2.0.6526 Final Is A VeryPowerful And New Tool To Deal With Types Viruses, Trojans,Worms, Malware And Other Malicious Tools That Prevent YourSystem From Hacking And Spyware Attacks. Comodo Software SecureInternet Explorer Scans All System Events By Looking For YourProfessional
Download Malwarebytes Anti-Exploit Premium 1.11.1.45 + Crack
ScreenShots: Software Description: Malwarebytes Anti-Exploit Premium 1.11.1.45 Full Crack | Application ProtectionProgram Malwarebytes Anti-Exploit Premium 1.11.1.45 IsA Protection Program For Windows Software That Provides A SecureEnvironment For Applications And Browsers With Its ProactiveTechnology. This Software Scans Your Computer With Advanced SearchCapabilities And Eliminates The Types Of Malicious Programs ThatHackers Can Hurt Through Them.
Download> HiTek Software AutoKrypt v11.19 + Crack
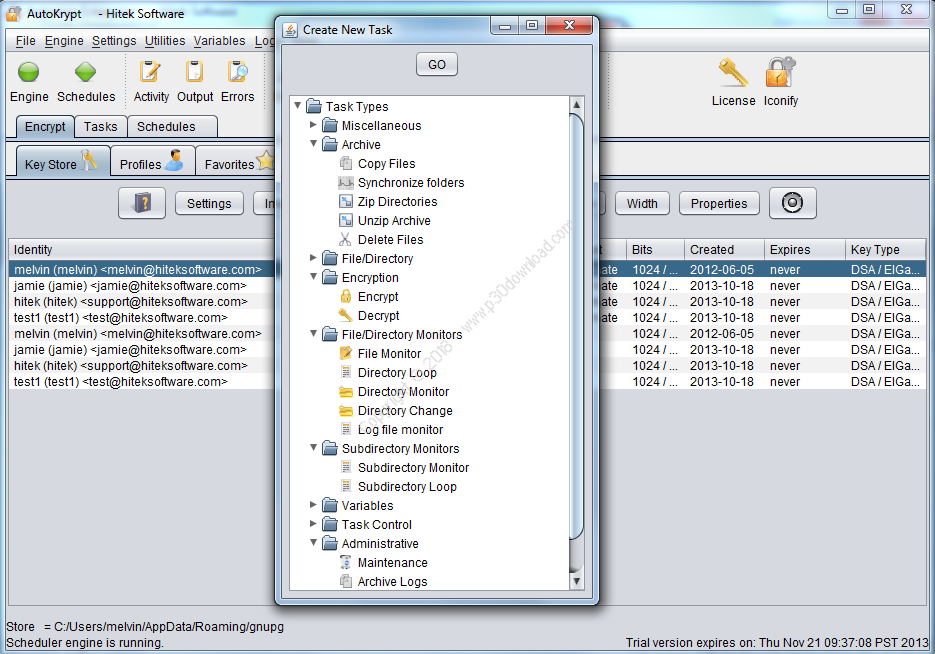
It’s always important to protect your files and folders,especially if you have a lot of sensitive information.AutoKrypt is a program that was designed toautomatically encrypt or decrypt files and folders. The app has asimple interface and a clean layout, making it easy to figure outby all users. As mentioned, the program can encrypt and decrypt
Download Avast Free Antivirus v17.8.2318 Keygen Serial
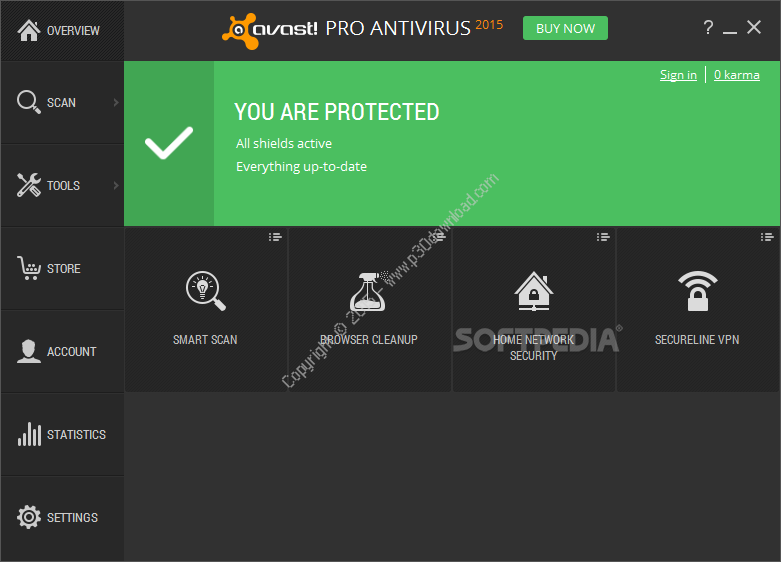
ScreenShots: Software Description: Avast Free Antivirus v17.8.2318 + Internet Security + Premier v17.9.3761 + Pro Antivirus v17.1.3394.0 Full Crack Avast (styled “avast!”) is a name brand for aset of antivirus software developed by AVAST Software s.r.o. forMicrosoft Windows, Mac OS X, Android and Linux users. The softwareproducts have a user interface available in 45 languages.
>Download Elcomsoft Forensic Disk Decryptor v1.0.110 Keygen Serial
Perform the complete forensic analysis of encrypted disks andvolumes protected with desktop and portable versions of BitLocker,PGP and TrueCrypt. Elcomsoft Forensic DiskDecryptor allows decrypting data from encrypted containersor mounting encrypted volumes, providing full forensic access toprotected information stored in the three most popular types ofcrypto containers. Access to encrypted information is provided inreal-time. Here are